Frequently asked questions
Datplan’s FAQ or Frequently Asked Questions page for Cyber Security and Cyber Control.
1) What is the difference between the free and licensed versions?
2) Is Cyber Control an Anti Virus Software?
3) Does Cyber Control hold personal information?
4) I get a security warning when downloading the software
5) How do I receive my license key?
6) What types of data can be uploaded?
7) Are all items flagged in the fraud list fraudulent?
8) A file password was found, what is the password?
9) What type of businesses should use this software?
10) Do you provide seminars or training courses?
11) What are the software Prerequisites?
12) Can the cyber risk control software be used on Mac?
1) What is the difference between the free and licensed versions?
The Full licensed version gives full access to all reporting and areas of the Cyber Control solution such as:
- Data uploads can reach over a million transaction lines
- Full access to the Cyber security fundamental whitepapers
- Full system review tools
- The Free version has a limitation placed of uploads up to 150 transactions
- Project plan can be exported, and amended and adjusted to meet business individual requirements
- License can be purchased here
The trial/free version limits areas of the Cyber Control solution. These restrictions are:
- Data uploads restricted to 150 transaction lines
- Reduced access to the Cyber security fundamental whitepapers
- Limited system review tools
- Project plan is read only
2) Is Cyber Control an Anti Virus Software?
No. Cyber Control is to be used alongside Anti Virus, firewalls and other security solutions. Part of the cyber security risk control framework recommends installation of a recognised Anti Malware solution. Datplan has partnered up with ESET who are an industry leading anti-virus and internet security provider to give Datplan’s clients the maximum protection against online threats. Please contact us for more information and promotions.
3) Does Cyber Control hold personal information?
To aid compliance with GDPR and Data privacy regulations, all data loaded by the user is deleted after every session of Cyber control is closed. Secondary checks are also in place to ensure loaded data is not stored for longer than is needed for the review to take place. An encrypted version of the email address of the license holder is held as part of license authentication. Any data input into the project plan is subject to the end users company data privacy policy. All data is held on the local machine the software is installed on and is not electronically transferred.
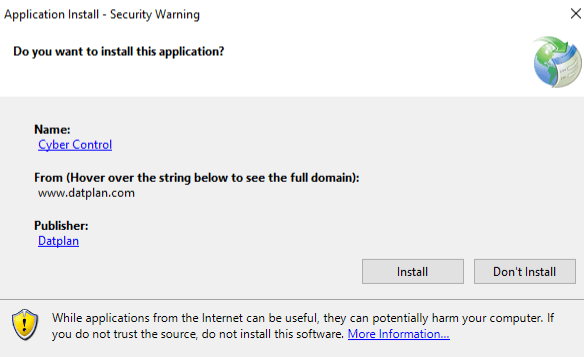
4) I get a security warning when downloading the software
.exe files are often flagged by both the internet browser and the Windows operating system to avoid a user downloading malicious content. This was introduced as another fight against the cyber threat by Microsoft (smart screen) and warnings on executable downloads by internet browsers.
What should you do if you see this warning.
The following methods should be undertaken on all types of instalation downloads from any source.
1) Ensure the download has come from the software vendors website or other noted distributor. In this case www.datplan.com
2) If in doubt scan any downloaded executable/set up file with an anti virus scanner before installing.
3) Ensure the publisher is NOT ‘Unknown’. You should expect to see ‘Datplan’ as publisher.
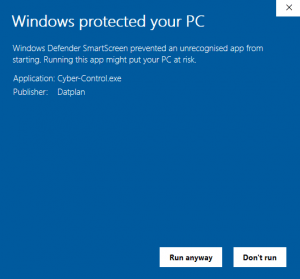
4) If the blue Smartscreen window appears. Choose ‘More info’ and again check that the Application is ‘Cyber-Control.exe’ and the Publisher is ‘Datplan’
5) If steps 1 – 4 have been passed then click ‘Run Anyway’ to install the application. It is good practice to follow these steps for all application instalations
5) How do I receive my license key?
Once the purchase has been completed a license key will be sent to the email address given on the payment form
6) What types of data can be uploaded?
Supported data files for uploading transaction data-sets are: Excel, Access and CSV file formats
7) Are all items flagged in the fraud list fraudulent?
Flagged transactions are potential risk items in a dataset based on the fraud detection criteria. These can include false positives where a legitimate transaction meets this criteria however any remaining items should be reviewed as they are considered not part of a natural dataset or form part of the reporting suites criteria.
An example would be; A manager has to sign off all expense transactions over $500, A dataset containing many transactions at $499 may be an attempt to make purchases outside of the sign off policy. However within this value there could be a legitimate purchase for this value.
8) A file password was found, what is the password?
Cyber control will flag a found password but not disclose it. Disclosing any password goes against the very nature of the cyber control solution and also avoids the software being used as a file cracking tool.
9) What type of businesses should use this software?
• Any business that holds private information and subject to data privacy and GDPR laws that needs to implement a cyber security and data security policy.
• Any business that records expense transactions such as; staff expense recharges, business purchases, holds credit card or bank account statements, logs petty cash receipts, record sales receipts and refunds. Individuals or companies that could be open to fraud.
• Cyber Control can run on datasets holding over a million records and so is suitable for all company sizes. Bespoke field mapping allows data to be loaded direct from a companies dataset without prior manipulation.
• Accountants, Auditors and forensic accountants use Cyber Control to run over their clients data to obtain test samples. Part of the reporting suite also allows random sampling of data records.
10) Do you provide seminars or training courses?
User Education is one of the key cyber security focus points and so training courses can be prepared. Datplan’s Coffee Book Range of publications gives a company the fundamentals to create in-house training. Software user guides are available on datplan’s YouTube channel
11) What are the software Prerequisites?
All software runs on base platform. At a high level this could be Windows or Mac operating system. At a more granular level within the operating system there is the Microsoft .net framework that applications may need to run on. Over time there has been many updates to the .net framework and applications may be tied to a particular version and so a user could have multiple versions installed. Cyber Control runs on the Microsoft .net 4.6 Framework and during set up will install it directly from the Microsoft site. Additional prerequisites are Visual C++ 2015-2019 which again is downloaded directly from Microsoft, Microsoft Access database Engine is also required to provide functionality with Office product installed. If in doubt these products can be downloaded manually from the Microsoft site. Although not essential to use Cyber Control, it is beneficial to have installed Excel and Access 32 bit installed for full functionality.
12) Can the cyber risk control software be used on Mac?
Cyber Control Centre is only available for Microsoft Windows

